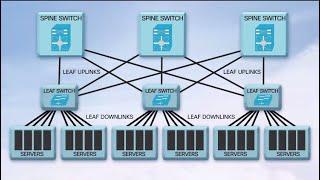
Learn how you can easily deploy whitelist policy to any network controller using JSON, XML or YAML formats.
To learn more, visit: http://cs.co/9004DRnKn.
To learn more, visit: http://cs.co/9004DRnKn.
- Category
- Cisco Systems
Be the first to comment
Up Next
Autoplay
-
Cisco Tetration: Security Policy Enforcement
by Cisco 202 Views -
Overview: Difference Between Whitelist and Blacklist Policy in Cisco Tetration
by Cisco 216 Views -
Overview: How to manage segmentation policy with Cisco Tetration
by Cisco 281 Views -
Cisco Tetration Policy Validation and Analysis
by Cisco 312 Views -
Cisco Tetration Policy Enforcement Overview
by Cisco 221 Views -
Cisco Tetration Policy Lifecycle
by Cisco 221 Views -
Cisco ACI and AlgoSec: Security Policy Management for the Next Generation Data Center (Demo)
by Cisco 236 Views -
Cisco Tetration Policy Ordering
by Cisco 352 Views -
Cisco Tetration Workspace and Policy Introduction
by Cisco 273 Views -
Demo: Cisco Tetration Automated Policy Recommendation and Simulation
by Cisco 280 Views -
QSFP28 100G Optical Transceivers in the New Data Center
by admin 495 Views -
How much is a 100G QSFP28 transceiver?
by admin 397 Views -
How about the feature of QSFP28 QSFP+ SFP+ XFP CWDM DWDM BIDI module? (LD, PD, Tx Power, Rx Sens )
by admin 408 Views -
Finisar Demonstrates 100G QSFP28 ER4f Transceiver at ECOC 2017
by admin 409 Views -
QSFP28 100G testing between Arista and Huawei
by admin 429 Views -
QSFP28 100G Transceivers in the New Data Center
by admin 460 Views -
Unboxing and Replace QSFP Broken || JNP QSFP 100G SR4 || SFP Module || Juniper
by admin 507 Views -
100G Transceivers Development
by admin 323 Views -
QSFP28 100G Transceivers: Key Features and Applications
by admin 646 Views -
Finisar QSFP28 Family Transceiver Demonstration at OFC 2015
by admin 430 Views
Add to playlist
Sorry, only registred users can create playlists.